
Out in the open: the summit between President Obama and China's Premier Xi was the first to actively address the issue of cyber attacks openly between the two countries at the highest level. Mr Obama provided Mr Xi with specific details of theft of US intellectual property “It [cybersecurity] is now at the centre of the relationship; it is not an adjunct issue. They understand clearly the importance of this issue,” said Tom Donilon, President Obama's outgoing National Security Advisor. © Reuters
The Internet's growth around the world has been staggering. In 1993, it is estimated to have communicated around 1% of the information flowing through two-way telecommunications networks. By 2000, that had leapt to 51%. By 2007, the figure had reached over 97%. Cartoon by Rytis Daukantas.

The importance of cyber skills was highlighted recently when the US CyberCommand announced plans to increase its personnel from 900 to 5000. The need to encourage and foster lacking IT skills is also being discussed by several NATO governments. Cartoon by Rytis Daukantas.

The Internet can be one of the great equalisers. At a recent hackathon, Jennie Lamere was the only female participant and the only one under 18. She won. Her hack was designed to help people avoid tweets which would reveal the endings of their favourite programmes before they had the chance to see the programme. She first got interested in hacking three years ago.

Hackers don't always act on interest or reward. Sometimes, they can be acting in a national government's interest. And in Iran, which was itself hit by the Stuxnet worm, there is such a group. It's called the Iranian Cyber Army. While it hasn't been confirmed that all the hacktivists working for it are Iranians, the group's work certainly supports the country's government. The sites the army have attacked include the US Voice of America, Twitter and the Chinese search engine Baidu.

Not all hackers should be feared. 'White hat' hackers describes those who look for weaknesses and loopholes in computer codes of key infrastructures - but then reveal this to the owners of these infrastructures. The idea is that if white hackers can tell organisations where their weaknesses lay, there is less opportunity for more malevolent hackers to exploit them.
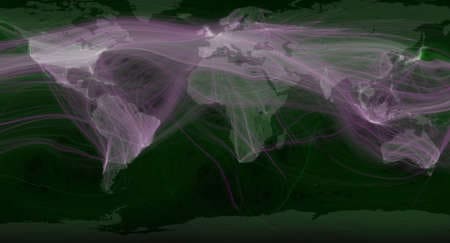
So who is the most vulnerable? This map shows Twitter traffic across the globe. It reveals that most of the traffic comes from major population centres. The recent hacking of President Obama's Twitter feed shows the vulnerability of some social media. The President's feed posted a false tweet by hacker which claimed that the President had been injured in a bomb attack. After the tweet surfaced, the Dow Jones industrial average fell more than 100 points in just two minutes. © Eric Fisher / Fast Company.

And it's not only youngsters who can use cyber skills. Shortly after 9/11, Shannen Rossmiller, a 31 year old mother of three in remote Montana, decided to fight back using the Internet. She signed up to learn Arabic, registered a false identity on al-Qaeda websites and got into conversations with extreme Islamists. By August 2002, she had convinced a Pakistani arms dealer that she was interested in buying weapons. When he offered to sell her Stinger missiles, she turned the information over to the FBI. She has also supplied government agents with hundreds of e-mails and backgrounds on dozens of foreign terrorist suspects.
